A high-quality building access system will enhance the security of your sites.
This guide to will show you how to ensure the safety of your revenue-generating equipment.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayYour buildings contain important gear and resources. If you haven't deployed an electronic alarms door alert system, you're not doing everything you can to protect your valuable building contents. Installing door sensors for comprehensive door alarms provides an extra layer of security, safeguarding your building's critical equipment. Reading this article is a good first step to prepare your door security system project.
A door alarm and control system, as the name implies, is composed of two basic parts.
First, you'll monitor your doors with an electronic alarm system. Note that this is not the same as a home security system - some of them are now DIY stand alone door alarms. These systems can also incorporate door or window alerts to provide holistic entry monitoring. You may or may not use some elements like a loud alarm bell and siren. Either way, the key objectives here are:
By having door sensors in the door access control system you have in place, you'll be alerted whenever a remote door is opened without proper authentication or at a specific time of the day or week. You can also set up your door alarm management system to directly alert the police or your own Security teams.
Authentication brings us to the second key component of the system: electronic door control. While monitoring door alarms is nice, an electronic door control alarm system is a good step to you can make toward maintaining security at your remote buildings.
Physical metal keys are outdated. Keys can be easily copied. Keys can be given away. Keys can be lost.
Keys may be used at any time of the day or night, regardless of how bad access in the wee hours of the morning might seem.
By integrating alarms door mechanisms, you reduce the risk of unauthorized access during non-business hours.
An electronic, database-driven access control solution solves each of these problems. Proxy key cards are much harder (bordering on impossible) for the average person to copy.
A proximity key card that is given away or lost can be shut off within the access database instantly. Proxy key cards can be limited to certain hours of the day and week. This reduces your vulnerability to after-hours intrusions.
Proximity cards can also be set to expire at a pre-set time. These allow you to give authorized visitors temporary access to your buildings. Pairing this with alarms door capabilities ensures that all access events are recorded and monitored. If a contractor is expected to finish a job within three days, for example, you might set his key to expire in four days and to allow access to a single door only during normal business hours.
A good security alarm system also includes a variety of related security systems. For maximum efficiency, systems should integrate door or window detection with IP cameras. For example, monitoring infrared motion sensors go hand-in-hand with door monitoring. It's also common to have IP cameras pointed at your front doors to provide more detail about the person entering your building.
In fact, a good IP camera can trigger automatic frame capture and archiving whenever a door alarm or motion sensor is tripped. What's more, it's even possible for an IP security camera to pull frames out of its temporary buffer when such an alarm occurs. In this way, you can actually archive a number of frames before a triggered event occurs, then a number of frames after the triggered event occurs.
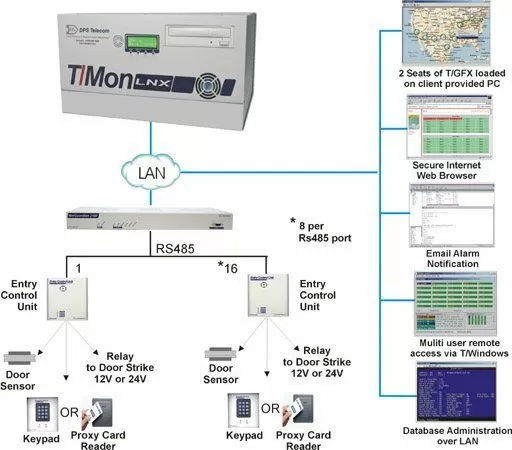
One good example of a secure door alarm and control system is the Building Access System from DPS Telecom. The core of the system is built around the Entry Control Unit (ECU), a small box that sits inside your buildings near the doors you want to alarm and control. The ECU accommodates an electronic door lock (either an electrically actuated strike or a magnetic plate) connected to the door control, a magnetic door open sensor to trigger door alarms, and 2 keypads and/or proximity card readers.
How you send alarms back from your ECU depends on the scope of your door alarm and control system. You might have just a few doors (maybe you're just controlling entrance to your server room, for example). It's quite possible that you'll use the ECU's built-in web interface to manage all door alarm alerts (email/phone/SNMP) and authorized user keycards/keycodes.

If you have a larger system, however, it's much more likely that you'll manage many ECUs using a central T/Mon master console. T/Mon is a central server for network alarm management and BAS management. T/Mon is an important tool for anyone using more than a handful of ECUs. It provides a means to database authorized users a single time and then broadcast those authorized user files to every ECU in your network.
T/Mon is also a good way to monitor door alarms in a larger door control scheme. T/Mon can be used to filter unimportant alarms and send you only the suspicious alarms that require human attention. T/Mon will still log all entries and exits to help you look at events after an incident has occurred.
One important facet of the BAS stems from its origins as a network management accessory. DPS Telecom started by specializing in remote monitoring and control systems for network staff. The Building Access System made sense because it provided physical security and monitoring for servers and other network assets.
Of course, DPS was asked by users who only wanted to use door alarm and control and had no network to monitor. This led to the development of standalone door alarm and access control systems that did not include the features (or the cost) of a full-fledged network monitoring system.
Today, this means that you have a lot of choice and opportunity if you choose to deploy the DPS Building Access System. If you only need to alarm and control doors, the T/Mon BAS and/or LAN-based ECUs will provide dedicated door alarm and control without any of the remote network monitoring features that you will never use.
If you do have a network spread out across a variety of remote sites (a certainty if you work for a telco, utility, or transit company), the BAS presents an opportunity for you to "kill two birds with one stone".
In this case, it would be ideal for you to purchase the T/Mon LNX instead of the T/Mon BAS. This is the full-featured network alarm management platform that will allow you to monitor and control your doors, your network gear, and environmental alarms like temperature and humidity from the same central console.
Technical advisors at DPS often receive requests for door alarm systems and information. Here's an example of one such request, which should help to focus your thoughts as you prepare for a door alarm deployment.
"Shaun, we do have the ability to execute these projects separately, but it will be more cost-effective (and require no extra time) to complete some of them simultaneously.
Given the likely scale of the final solution, I want to do a pilot first at the HQ.
Please provide info and a quote for door access control for the main server room. This should comprise (to my untutored mind) the electronic locking mechanism, a proximity card reader and an initial 20 proximity cards. We'll need the software to program the cards and system and to log the traffic.
The remote boxes of your Building Access System are also capable of environmental monitoring. I recommend that we take care of both server room access control and server room environmental monitoring in the first phase of the project.
This advantage does not exist for the private areas of the bank and the clock-in system. These could be done efficiently in later phases.
The bank has 22 branches currently, please consider 25 as the initial number to be covered. The server rooms all have only one door.
At this stage I think it sufficient to monitor only the ambient temperature. We may monitor single equipment at a later stage. Humidity may be of interest."
Here's another request for you to consider.
Jon has an interest in the Building Access System. They have something similar, but it's not integrated with alarm monitoring. Their techs would "love it". Also had an interest in Stay-Open Mode for remote sites, so technicians can unlock a door for several minutes or hours until they complete the job.
Jon wants to learn ASCII rules so he can modify them to bring in more detail about the exact card that has failed or the customer(s) affected. He wants to integrate a lot of disconnected systems into one overarching monitoring system.
The company is looking for a new trouble ticket system for logging work performed on a single equipment, for specific customers, and/or by specific employees.
Recommended Door Alarm and Control Gear
All DPS Telecom products include comprehensive technical support. If you've purchased one of our products and are encountering any kind of issue, contact DPS Tech Support today at 559-454-1600.
At DPS Telecom, the representative who answers your call isn't an intern reading from a script. DPS Tech Support representatives are engineers who contribute to product development. And, if your problem requires additional expertise, the DPS Engineering Department that designed your product is right down the hall.
Help us connect you to the right engineer by filling out this quick questionnaire. Simply leave your contact information to get started, and we'll call you back. Most preliminary discussions are about 15 minutes, and afterward, we'll send you a custom application diagram of a recommended solution that'll make it easier to justify your project to management.