Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayThe world is going through changes now more than ever and it relies immensely on technology and on digital communications. This also means that network security became very important.
When you need to protect your network and safeguard your mission-critical data, having blind sports is one of the biggest security challenges you will face. That's especially true if your company have Supervisory Control and Data Acquisition (SCADA) systems.
With SCADA systems, you are able to not only gather sensitive information but also control your mission-critical equipment. So, if the wrong people access your system irreversible damage can be done. That's why network visibility is vital for most companies.
So, let's talk about about what exactly network visibility means and how it will help you protect your system against security threats.
Network visibility can mean multiple different things in different processes and activities. But, in terms of remote monitoring and control systems, network visibility is the ability to have situational awareness over all aspects and components of your network.
In order to achieve network visibility, companies put in place monitoring solutions that are used to manage their system. Some of these elements are:
This is just a short list of what remote monitoring solutions are capable of keeping an eye on. Also, when deploying a SCADA solution for network visibility, you can control and make changes to your system according to the information collected.
With a network visibility solution in place, the security of your system will be improved as you will be able to proactively detect any early signs of network compromise. This allows you and your technicians to act towards preventing issues and not waiting for incidents to happen in order to respond.
Better network visibility also gives you better network analytics capabilities, which allows you to make informed decisions about your system protection and business strategies.
There are multiple reasons why having efficient network visibility is important.
As we've talked before, blind stops in your network are an open door for cybercrimes. Having unknown vulnerabilities can potentially give individuals with malicious objectives easy access to your network.
That's where network visibility comes in. It keeps you informed and helps you detect any weaknesses within your system, these capabilities are a vital part of protecting your data and controls.
A network visibility solution will allow to keep a close eye on the traffic passing through your network. So, for example, a network monitoring tool might give you visibility by notifying you about unexpected situations and conditions, such as slow network response. With immediate and detailed alerts, your technicians will be able to take action in a timely manner to solve any problems that arise.
Another benefit of having network visibility is the ability to monitor your processes and applications. Most companies utilize many different processes that allow them to provide mission-critical services. With a network visibility solution in place, you will gain insight into what is happening during your processes and into the status of your network performance.
There are many other advantages when using network visibility systems, but all of them will ultimately make your system's performance more efficient and will allow you to ensure your company is protected.
To protect your system, make sure that your network visibility solution supports important security features. Some of them are:
If your network visibility system can be accessed via a web interface, then make sure that your information and control relays are protected. This is especially important if you work for a governmental agency or any other security-conscious organization.
The HTTPS/SSL encryption will make sure that your sensitive data is secured.
Remote Authentication Dial-In User Service (RADIUS) is used as an access server authentication and accounting protocol. It uses the client/server format and passes user information to designed servers and acts on the response that is returned.
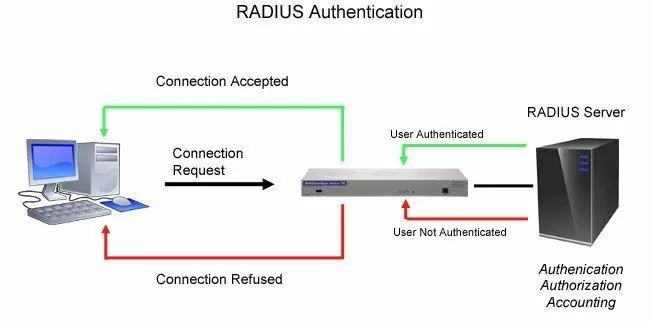
Receiving client requests, authentication of the user, and the return of configuration information required for the client to deliver services to the user are some of the tasks performed by the RADIUS server.
Many organizations already make use of RADIUS servers in their network. This is because these servers are an efficient way to centrally manage user access rights and passwords.
Make sure your monitoring system is able to smoothly integrate with any standard RADIUS server, so you can have a central location to administer logins to many different types of equipment.
Sometimes knowing who to trust is better than keeping a blacklist. This means that, with IP filtering, you can limit access to your monitoring system to only the specific IP addresses you trust. This is a very efficient way to cut down your system's vulnerabilities.
Modem dial-back is a simple technology, but if used in the right way it can become very useful.
If your network visibility system devices support modem dial-back, then they can call you whenever they've been accessed. Under usual circumstances, you'll receive a call after you or your techs have made a change to your system. But, if you get a call that you were not expecting, then you know that someone other than you or your team accessed your system.
One important aspect to avoid is giving "all or nothing" access to your system users. Since it only creates more security risks than necessary, it's way better to give your staff only as much access as they need to do their particular jobs.
So, if an internal incident occurs, your list of suspects will be way shorter.
When any kind of accident happens, it's important to have some kind of logging report to refer to in order to identify what occurred.
Make sure your network visibility system is able to log the user ID for alarm acknowledgments and other activities. This way you'll know if any authorized activity happened and when they occurred.
Unauthorized people usually depend on your usage of standard ports for certain types of traffic.
So, it's important to have a system that allows you to choose a custom port for different jobs, this makes you immune to many threats that make use of common ports.
A problem that many companies have is allowing each member of their team to choose any password as they seem fit.
Why is this a problem? Because you'll probably end up with week passwords that are nothing more than short, simple words. And that's the scenario that any hacker dreams about. So, make sure your network visibility system allows you to have the option to require a strong password. A strong password usually have a minimum length requirement and mandatory character types.
Normally when someone wants to access a system that they don't have the login information, they send multiple sorts of requests until they get it right. However, if your remote monitoring system doesn't provide them with a reply, the unauthorized person won't know what to expect.
The dark answer feature makes it so your equipment will issue no apparent login prompt. Only the authorized users will know that the system is, in fact, listening for the username and password, So, after you log in, your system should respond as usual.
SNMPv3 is the third version of the Simple Network Management Protocol (SNMP). This latest version supports encryption for the secure transmission of data. SNMPv3 security comes mainly in two different forms:
Other than supporting the previous tools, your network visibility solution needs to provide you with monitoring and control best practices.
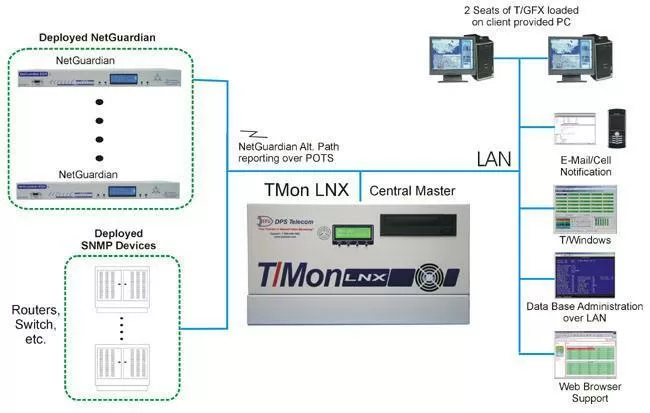
Finding network monitoring devices that follow visibility best practices is key to have an efficient system. One example of a competent device that will provide you with top-notch visibility is the T/Mon master station.
The T/Mon master provides a centralized graphical interface that helps you achieve complete visibility over your network. With a visual representation of your network, you can spot any issues in a timely manner.
Its dynamic and user-friendly display is a favorite in the market. Anything you need to do, you can get done fast. These tasks usually include things such as remote monitoring, remote control, information backup, security management, and report management.
T/Mon also helps you troubleshoot issues, as it gives you detailed trend analysis and root cause analysis capabilities. Those features allow you to track every alarm within your network both historically and in real-time. This will significantly reduce the time you would spend troubleshooting because it gives you a detailed timeline of your network alarms.
This master station allows you to manage tens of thousands RTUs and any other network equipment, and since it has multiprotocol support you can smoothly integrate all your devices under one umbrella. This maximizes your security and efficiency.
T/Mon offers more than monitoring capabilities, it allows you to remotely control, administer, and customize your system through one single intuitive interface.
If you've ever been the victim of any type of network intrusion, then you have a pretty good idea just how important network visibility is. And, if you are reading this article, that's a concern you are trying to eliminate.
There are many remote monitoring vendors in the market today and it's important to research all your options and know exactly what you'll be getting for your money. That's because not all vendors will provide you with features to properly secure your system.
Here, at DPS, we aim to rise to any challenge you might be facing and our remote monitoring solutions are proven to help technicians manage complex networks. Our RTUs and master stations are custom designed to meet our clients special requirements, and come with a wide range of capabilities that will help you eliminate security challenges.
If you would like to know more about our devices and try them out, all you have to do is reach out to us.

Morgana Siggins
Morgana Siggins is a marketing writer, content creator, and documentation specialist at DPS Telecom. She has created over 200 blog articles and videos sharing her years of experience in the remote monitoring industry.