Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
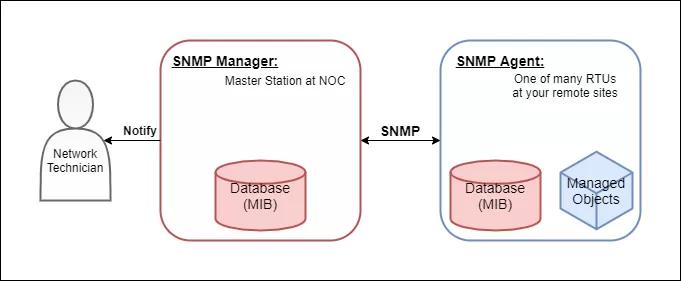
Reserve Your Seat TodayIf you work with SNMP monitoring, you've probably heard terms like "Trap," "Get," or "Inform" tossed around casually. Maybe you've even skimmed a protocol diagram or poked around your SNMP manager. But do you really know what's inside those packets your devices are sending?
If your answer is "not quite," you're not alone. Most SNMP guides skip the fundamentals of the actual packet structure. This leaves you in the dark when your manager stops showing alarms - or worse, shows the wrong ones.
In the next few minutes, you'll get the clarity you've been missing. We'll dive inside an SNMP packet, understand the different types of messages, compare Traps to Informs, and review how SNMP versions impact your network security.
Along the way, you'll see how this knowledge helps you avoid several major headaches and build a "bulletproof" monitoring setup.
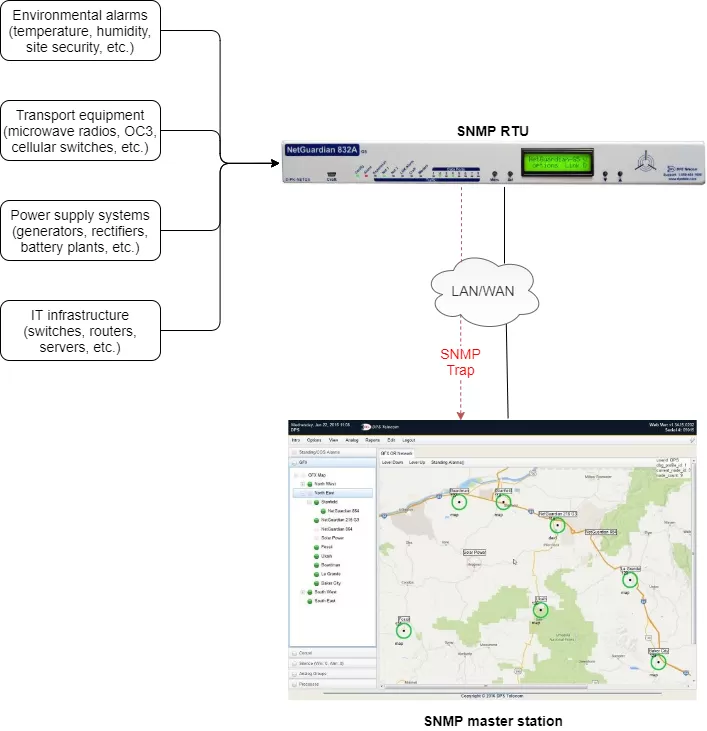
Let's say an important generator at a remote site shuts down. Your SNMP manager should alert you - but you don't see anything.
This is where the trouble sets in. Is the generator offline? Is the alarm stuck? Is the SNMP Trap even getting through?
These questions can't be answered by just looking at your monitoring dashboard if something has gone wrong.
That's why understanding SNMP packet structure is so important. You need real visibility. That sometimes means you have to get into the "nuts and bolts" of SNMP to fix what's wrong.
Imagine you're debugging an problem-to-notification flow. With full SNMP packet knowledge, you:
That kind of expertise turns you from a "reactive responder" into a proactive architect of your reliable monitoring system.
When everything works, SNMP can remain invisible. But when it breaks, your ability to read and diagnose individual messages is the difference between a 2-minute fix and a multi-hour rabbit hole.
Let's peel back the layers a little bit.
Every SNMP message (formally called a Protocol Data Unit, or PDU) travels over two layers of network transport:
Once you strip away that outer wrapping, here's what you'll find in a typical SNMP packet:
| Field | What It Does |
|---|---|
| Version | v1, v2c, or v3 |
| Community String | Acts like a password - authenticates access |
| PDU Type | Get, Set, GetNext, GetResponse, Trap, or Inform |
| Request ID | Tracks command-response flow |
| Error Status/Index | Indicates success or failure |
| Variable Bindings | The actual data - Object Identifiers (OIDs) with values |
Pro tip: The Variable Bindings are the payload. If they're missing or malformed, even a "valid" Trap is just noise. This is where your alarm information lives - unless you're using "Granular-OID Traps" where every possible problem has a unique OID.
For a real-world troubleshooting scenario, Variable Bindings are where you'll check the OID structure and its corresponding value to confirm that your SNMP agent is sending what you expect. If your voltage reading is "0" instead of "-48," this is where you (or your SNMP manager in most cases) will catch it.
There are six main PDU types in SNMP, but only a few matter in day-to-day alarm monitoring:
Gets and GetNexts are used by your SNMP manager to request data from a device. For example: "What's the battery voltage at Site 7?"
GetNext is used when the exact OID isn't known. Think of it like scanning through a table of values, one row at a time.
Sets are sent by the manager to change something. These are often to trigger a relay or reset a flag. For example: "Close relay 2 at Tower B to start the backup generator."
GetResponse is your device answering a Get or Set command with actual data. If something goes wrong (like a malformed OID), this is where the error code shows up.
Traps are sent unsolicited (asynchronously) from a device to notify the manager about an event. For example: "Door sensor tripped - possible intrusion!"
These are what you depend on for real-time alerts, although a device failure may not be promptly detected. That's where polling-based strategies involving "Get" messages on a polling loop become useful.
An Inform is like a Trap, but better. It includes a response from the manager to confirm receipt.
These are used for events that require accountability and confirmation. Such events include system-wide failures and high-priority alarms.
Here's a quick head-to-head comparison:
| Trait | Trap | Inform |
|---|---|---|
| Direction | One-way (no reply) | Two-way (manager replies) |
| Overhead | Minimal | Higher (extra traffic), usually no big deal |
| Reliability | Low (no ACK) | High (requires ACK) |
| Use Case | General alarms | Critical alerts |
Possible example: If you're monitoring a door sensor, a Trap is fine. But if a fire suppression system activates, you'd better send an Inform since you need to know the manager received it. But, in the real world, Traps are far more common than Informs in default device configurations.
At DPS Telecom, many of our remotes - including the flagship NetGuardian 832A G6 - support both Traps and Informs. That gives you the flexibility to balance performance with reliability, based on your network's needs.
SNMP has evolved significantly since its early days. Let's break down the three versions and when to use each:
| Version | Security | Use Case | Use It? |
|---|---|---|---|
| v1 | None | Legacy systems | Avoid if possible, but using might be OK on secured networks. |
| v2c | Community string only | Lightweight, simple setups | OK in trusted networks |
| v3 | Full encryption & auth | Secure environments | YES - especially when layered security matters |
Key SNMPv3 features are:
If your network spans public or shared infrastructure, you should be using SNMPv3. It's more complex, but worth it to protect your monitoring data from spoofing or eavesdropping.
DPS remotes like the NetGuardian LT G2 and NetGuardian M16 G2 support SNMPv3 natively, ensuring your alarm data stays secure from edge to core.
If your SNMP manager isn't displaying alarms - or is showing bad data - it's almost always one of the following:
Tools that can help with this are:
You don't have to memorize every possible failure mode, but you do need to know how to inspect the message flow. SNMP tools make that process visible - if you know where to look.
At DPS, we've been designing SNMP-enabled alarm remotes for over 30 years. Our devices aren't just SNMP-compatible - they're SNMP-aware. That means:
We've helped thousands of clients troubleshoot obscure SNMP issues. We're equipped to help you, too.
Knowing your SNMP packet structure isn't just for protocol nerds. It's how real professionals make real systems work.
By now, you know:
But reading is only the first step. The next involves applying this knowledge with the right gear - and the right team behind you.
Whether you're replacing outdated RTUs, adding SNMPv3 security, or just trying to decode a mystery Trap, we're here to help.
Call us now at 559-454-1600
Email: sales@dpstele.com
Talk to an expert who can walk you through your packet capture, recommend the right remote, and set you up with a real, working solution.
You just have to call.

Andrew Erickson
Andrew Erickson is an Application Engineer at DPS Telecom, a manufacturer of semi-custom remote alarm monitoring systems based in Fresno, California. Andrew brings more than 19 years of experience building site monitoring solutions, developing intuitive user interfaces and documentation, and opt...