Download our free Monitoring Fundamentals Tutorial.
An introduction to Monitoring Fundamentals strictly from the perspective of telecom network alarm management.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayWeb-based monitoring equipment offers one major benefit over older gear: you can configure and use it via any computer with a web browser. Simply by typing in the IP address of your alarm remote or master station into your address bar, you'll have access to a clean and clear interface for configuration and monitoring.
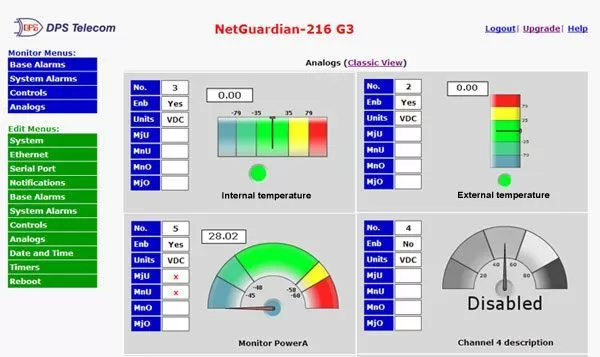
If you choose a monitoring device that's web-based, you won't need to worry about software installations. At best, those waste time. At worst, it can be really difficult at security-conscious organizations to get the right IT Department permission to install any software.
Should I choose a monitoring device that's web-based ONLY?
Probably not. While the web interface is an important component, it's a good idea to find a remote that can send you alerts using other methods. It might send you an SMS text message, call you on your phone with voice messages, or report to a central master station using SNMP, DNP3, Modbus, or another industry-standard protocol. In short, web interfaces are a handy tool (and they're all that you need to manage a small handful of sites), but it's always a good idea to have alternative options.
What happens when your network grows? Will your existing remotes be able to communicate with a newly deployed master station, or will you just have to throw them away and buy something else? Web-based monitoring devices may be the best choice for your size today, but eventually you may need the flexibility to grow into a centralized monitoring setup.
How can I tell the difference between a good web interface and one that will slow me down?
The goals of any web interface should be clarity and responsiveness. You can't afford to wade through confusing menus, and the flexibility of web technology means there's really no excuse for poor design anymore. Step-by-step web-based configuration wizards are available in some of the top-notch monitoring systems. They'll walk you through all necessary setup processes one step at a time with clear explanations.
You also need a system that's fast. Underpowered devices might, technically speaking, have a web interface, but they might be too slow to run it effectively. If you click "Submit", but then have to sit around for 45 seconds, you're going to waste a lot of your precious time. You need a monitoring device that's fast enough to deliver web interface pages quickly.
What monitoring data should be available in the web interface?
In short, you should be able to monitor every piece of collected data via a good web-based monitoring interface. Although the list will vary based on the equipment you've chosen, common items to look for include:
What things should I be able to configure and control via web?
Just as a good web interface allows you to monitor all of its collected data, it will also allow you to configure all relevant settings and execute control functions via the same web-based screens.
Configuration includes:
Is web access secure enough to use in sensitive corporate and government networks?
If you're running web-based monitoring equipment internally on a secured LAN, you may already have the full security layer that you need. But what if you want to access your monitoring device on the external Internet?
While some organizations have policies against any external access at all, others will allow it but require you to use a device that supports HTTPS (SSL) encryption. Since it requires more powerful hardware and superior engineering, only some manufacturers offer support for encrypted HTTPS connections to their web-based interfaces.
Whether you need encryption or not, it's always a good idea to choose a monitoring tool that requires at least a password (if not a username/password combination) to log in. While it does serve as reasonable protection against hacking and malicious programs, password protection also protects your lower-level staff members from accessing a web-interface without adequate experience and accidentally causing a major incident.
Recommended web-based monitoring tools: