Download our free Monitoring Fundamentals Tutorial.
An introduction to Monitoring Fundamentals strictly from the perspective of telecom network alarm management.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayCritical infrastructure protection is a growing concern worldwide. To protect against modern terrorism threats, governments have begun to define, support, and enforce standards for the protection of critical infrastructure.
Critical infrastructure includes all public and private systems that, if destroyed or otherwise incapacitated, would present a serious hardship to local residents. This includes power utilities, transit networks (including highways, railways, and air), water purification plants, the Internet, and similarly critical systems.
Since critical infrastructure is so important for the general welfare, governments have taken steps to protect it. This is usually handled through subsidies for security and protective technologies and followed by requirements to maintain certain minimum protection standards.
Remote monitoring plays an important role in just about every industry that contains critical infrastructure. That's because the very same systems that make infrastructure vulnerable to terrorism, a large geographic spread and hundreds of unmanned sites, also make it an ideal candidate for remote monitoring.
Remote monitoring of infrastructure and their supporting computer networks involves quite a range of sensor types. Of course, any system for the prevention of terrorism should include traditional "security" sensors like passive infrared (PIR) motion sensors and magnetic door sensors. These systems should also be conspicuous to act as a strong deterrent against would-be terrorists.
There are also active systems to reduce infrastructure threats, like electronic building access control based on keypads and proximity card readers. These are far superior to traditional locks and keys when it comes to limiting site access to authorized visitors.
But critical infrastructure protection involves much more than just the technologies used to stop burglars. Since the aim of infrastructure terrorism is to disable networks, a lot of protection is gained by monitoring the individual systems that make up the broader network. Is LAN active to all remote sites? Is your fiber ring operating normally? Are any sites experiencing a temperature rise that could lead to thermal shutdown. Effective monitoring for all of these conditions and more provide an effective detection mechanism against sabotage. Early warning of an attack in progress, even one that is sophisticated and synchronized, gives you the best possible chance of deploying security personnel or law enforcement to neutralize the threat.
Fortunately, government assistance is available in a variety of industries for the purchase and deployment of effective systems that improve critical infrastructure protection. What's more, these same systems offer operational advantages that can improve your bottom line. Improving your remote monitoring and site access control makes sense from every angle. You're helping to protect infrastructure that benefits the public while simultaneously improving your service levels and efficiency.
Critical Infrastructure Protection Equipment Examples
As I described before, traditional "security systems" just scratch the surface of good infrastructure protection. Still, they are certainly an important part of an overall system and warrant some discussion.
For electronic building access control and monitoring, the DPS Building Access System is a good place to start our discussion. It's especially appropriate in this case because of its integration with a network monitoring system, but first things first.
The Building Access System, depending on which remote box you select at each site, controls from 1 to 32 or more doors at each site. Users may enter controlled buildings by entering a code into a keypad and/or holding a proximity card near a wall-mounted reader. Access can be restricted at certain times of the day and week.
Access decisions are made by the Entry Control Unit (ECU), a small box mounted on the interior of the building near the door being controlled. After receiving direct input from the keypad or proximity reader, the ECU can check with devices higher up in the system hierarchy or, if communication is lost, it can make access decisions based on its own internal subset of the user database. If access is granted, hardware is activated/deactivated to allow entry. Most commonly, this takes the form of an electronically actuated door strike or a magnetic door lock.
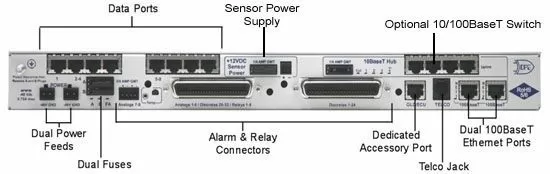
The Building Access System leverages your infrastructure of NetGuardian alarm remotes, so it makes sense to talk about them next. Alarm remotes are used primarily for remote monitoring whenever they're deployed, including in critical infrastructure protection scenarios, and the NetGuardian is no different. Even though it supports a building access control system as well (a rare feat for an alarm remote), it's still an alarm remote. The NetGuardian 832A model will collect equipment alarms from your mission-critical equipment, then relay them back to you so you can react. It also has 8 analog inputs for monitoring temperature, humidity, battery voltage, fuel level, and anything else that's best represented as a value within a continuous range, rather than a simple "on/off" indicator.
To remotely activate/deactivate equipment at your sites, the 832A is also equipped with 8 relay contacts. These can be used to activate backup lights and generators, or anything else, without having to waste time driving out to the site. To achieve a similar advantage, this alarm remote is also equipped with an 8-port serial terminal server. That allows the NetGuardian to provide remote connectivity for up to 8 legacy serial devices. Some modern devices also have serial access as a backup or maintenance method, and the terminal server allows remote access to those devices as well.
At the core of your critical infrastructure protection system is an alarm master of some kind. SNMP managers from a variety of manufacturers are common for use in telecom, utilities, and transit companies. For companies that have a variety of equipment from different generations, they need a solution to mediate a variety of different communication protocols into a single monitoring system. You can't protect your critical infrastructure effectively if you have multiple people (or, worse, a single person) looking at multiple incompatible monitoring interfaces. Something will be missed, and it could be a sign of a network problem or attack.
One solution that has won significant industry acclaim for integrating otherwise incompatible monitoring and management systems is the use of a multi-protocol manager or mediator. T/Mon is one such platform. It communicates with remote devices using over 25 protocols (including legacy and proprietary) and has the ability to forward alarms to an SNMP manager as SNMP traps. You may also use T/Mon as your top-level manager. In either case, you've effectively converted a disjointed mix of incompatible systems into a single cohesive monitoring system. This vastly increases your level of critical infrastructure protection.
T/Mon is beneficial to use as your top-level master station if you'd like to monitor your network using a geographic map display. The included T/GFX software is based on Microsoft MapPoint(R), so alarms are viewable on maps that can be zoomed and panned. Depending on the size of your infrastructure network, you can also create a full network view with icons for each region. Any alarm under a region will cause the icon to blink and the color to change to indicate alarm severity.
To protect your critical infrastructure, your technicians need to take the right tools for the job when they leave the central office. T/GFX facilities this by supporting custom uploaded photographs and images once you've drilled down to the site level. This means that a user can view equipment alarm icons on a floorplan of a building. After drilling down again, they could see individual equipment icons overlaid onto a photograph of the actual equipment in the rack. When was the last time your technicians had anywhere near this level of briefing before leaving the office. Imagine the positive impact that will have on their ability to provide critical infrastructure protection.
Critical infrastructure protection is a required part of doing business in the modern world. Fortunately, as I've explained, many business benefits can also be derived from the same systems that protect your infrastructure. A good monitoring system doesn't care whether terrorists or a failed HVAC system has caused your equipment to fail. It will report growing problems as they occur, so you can minimize the impact and, if service does fail, get service back online as quickly as possible.
Armed with this new knowledge, embrace the federal, state, and local programs available in your area for critical infrastructure protection. Just because something is a requirement doesn't mean it has to cost you. At its best, the government simply wants you to have the tools needed to provide reliable service. To the extent it will assist you with the acquisition and deployment of infrastructure monitoring systems, you should accept such assistance as a tool to improve your operational efficiencies.
For technical specifications of recommended infrastructure protection equipment, review these pages:
Master Station: T/Mon (includes T/GFX geographic map software)
Alarm Remote (RTU): NetGuardian 832A G5