Download our free Monitoring Fundamentals Tutorial.
An introduction to Monitoring Fundamentals strictly from the perspective of telecom network alarm management.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayHow much money do you have invested in your server room? What would it cost you if you were to lose all its functions due to environmental conditions your gear couldn't handle? The answer to both of these questions is likely, "a lot."
Being unaware of the status of your server room will cost you a fortune in the long run. Too many people try to save money now by leaving their gear unmonitored - only to end up with massive costs the instant they suffer a network outage.
The good news is the answer to monitoring your gear is simple. By using a remote terminal unit (RTU), you can monitor all of the factors that could damage your gear.
In addition to just the gear, monitoring the network traffic is essential for maintaining strong network security. Network traffic monitoring is so important because it provides real-time visibility into the flow of data across the devices in your network. By actively tracking network traffic, you can identify potential threats such as unauthorized access, malware, or suspicious activity that could compromise the security of your systems.
This monitoring helps in detecting anomalies that indicate an attack, such as unexpected spikes in traffic or data being sent to unknown external destinations. Additionally, it makes sure that sensitive data remains secure and that compliance with security regulations is maintained. Without traffic monitoring, you risk being unaware of malicious activity until after damage has occurred, making it a critical aspect of network defense. When defending your network, there are the six key threats you need to protect your computer server room gear from.
Computer equipment generates a lot of heat and, if the temperature of your server room gets too high, your gear will likely shut down due to overheating, bringing your entire network to a crippling halt. By using live analog sensors, you can monitor the precise temperature at all times - so you're always aware if there's a problem in your air-conditioned data center.
While humidity threats are much more unexpected than temperature threats, that doesn't mean they're any better. If the humidity levels are too high, you run the risk of water build-up on the components of your gear - which could lead to rust and gear failure. Humidity levels that are too low are also dangerous. Low humidity leaves your gear susceptible to static electricity, which could seriously damage your gear.
If a power outage happens to your server room, you need to know as soon as possible, so you can either restore power or get your backup generators going. You can't afford to lose power to your key networking equipment and find out later from your customers calling in and complaining. Don't leave yourself in the dark - monitor the power sources that are keeping your revenue-generating gear online.
If you rarely go into your server room then a slow water leak could steadily build up and cause severe damage. A few drops of water in the wrong place could short circuit several pieces of mission-critical gear, leading to network downtime and lost revenue. Using water detectors can give you an early warning when water is threatening your network.
One of the simplest, least expensive, and more effective ways to control the temperature of your server room is to use airflow management. By properly managing air circulation in your computer server room, you can regulate the temperature in a cost-effective way.
However, if there is a disruption to this flow, or one of your cooling units goes down, it won't be long before your servers execute thermal shutdowns. By using airflow sensors, you can be notified the instant the air in your server room isn't being properly circulated.
Your server gear is valuable, so it's absolutely key that you put in place physical security as well. This is especially important if you have gear located at a remote site that's away from your central office. With access controls, you'll be able to know the instant you have an unwanted visitor, avoiding damaging vandalism or theft.
By monitoring these six key threats, you'll be protected from preventable network emergencies that could have caused an outage - halting service to your customers and costing you tons of revenue.
Cybersecurity policies and training protect against these threats by significantly improving network security. These policies and training sessions establish clear guidelines for secure behavior and uphold that all employees are aware of potential threats. Policies create a structured approach to handling sensitive data, managing access, and responding to security incidents. They make sure that proper procedures are in place to mitigate risks.
Some of the procedures involved in preventing threats include password management, device usage, and data encryption. Training complements these policies by educating employees on the latest cybersecurity threats - such as phishing attacks and social engineering - and teaching them how to recognize and respond to suspicious activities. When everyone in an organization understands their role in maintaining security, the risk of human error is reduced. Together, well-defined policies and ongoing training create a proactive defense against cyberattacks.
Increasing network security also involves preventing access to untrusted sites. Here are some effective measures you can take:
By implementing these measures, you can greatly improve network security and prevent users from accessing untrusted sites.

Now you know how these threats can cost you a fortune in the long-run, and you're ready to do something about it. The good news is protecting your network doesn't have to be a hassle, and it doesn't have to break your budget. Using a combination of Remote Telemetry Units (RTUs), Master stations and sensors can give you the visibility you need to protect your server room and your mission-critical gear.
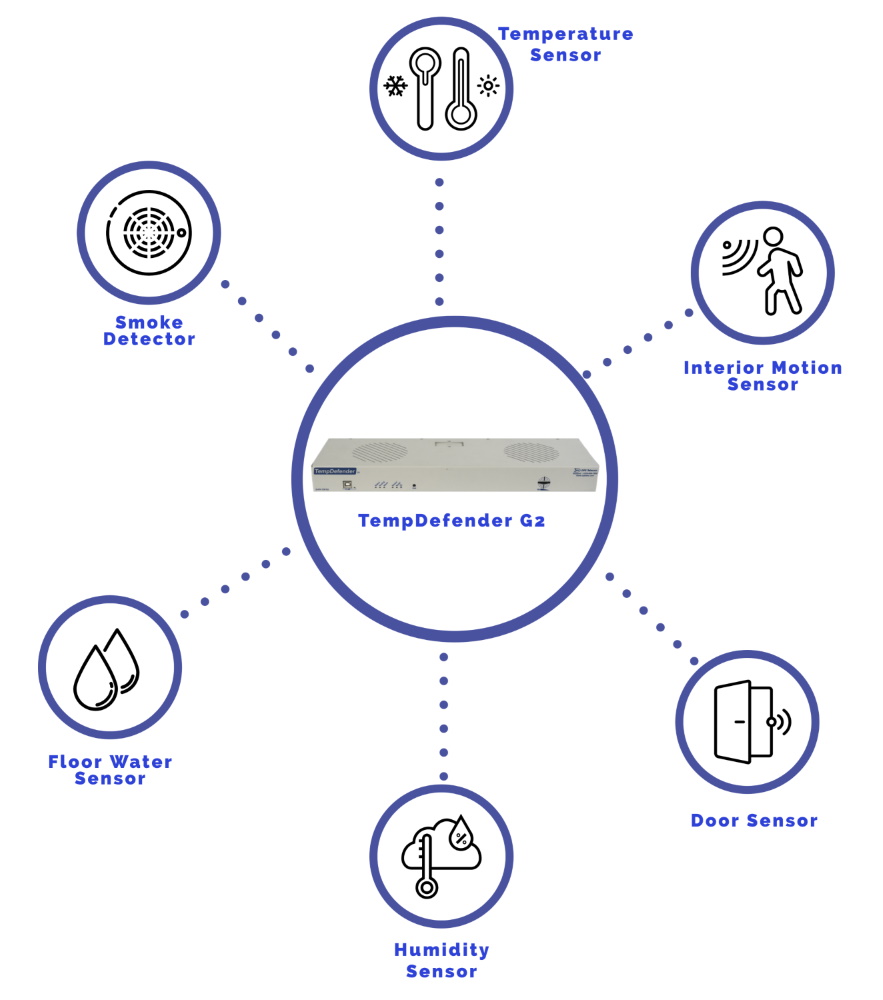
To monitor various spots in the server room from a single device, DPS Telecom makes the TempDefender. The TempDefender is a small, rack-mountable remote telemetry unit (RTU) that can handle up to 16 analog sensors reporting on all of the environmental factors in your server room.
Sensors for the TempDefender may be daisy-chained together, so you don't have to run a mess of cabling back to the TempDefender. You can also string sensors up to 600 feet away from the RTU, allowing you to run sensors to the most extreme spots in your server room from a centrally located device without worrying about connectivity issues.
Be careful if you measure your server room cooling system this way. Be sure to run sensors to spots likely to be hot. These include above equipment, hot aisles, and near your hottest racks.
You should also place sensors where air flow is most necessary. This can include hot air aisles on both sides of your cold aisles. This will ensure even cold air distribution.
You want to ensure that air, both cold and hot, is being effectively moved through the system. Losses and inefficiencies result in hotter server rooms and more energy expended in the cooling process - it's not as bad as a complete meltdown, but still not optimal.
If you're looking for a rack-to-rack solution, you should consider something like DPS Telecom's NetGuardian 216 G3 remote. The unit has four analog inputs, with which to measure the environment within the rack (or string sensors across a few racks) and 16 discrete alarm inputs so you can directly monitor your servers and other equipment.
The NetGuardian 216 provides a total solution with which you can monitor environmental sensors and the dry contacts coming directly from your servers, so whether your problem is environmental or otherwise, you'll know about it.
Picture how much easier your job would be with this kind of protection. Imagine - you'll never be the last to know about a threat to your gear. Having the ability to prevent many network outages doesn't have to be a dream - you can make it a reality.
The first step to protecting yourself against damage is to make sure you have the right info. Too many monitoring systems don't see the big picture and leave out vital features that can mean the difference between an outage and network up-time. In order to learn about the basics of network monitoring, I recommend downloading the free Server Room Monitoring Tutorial White Paper.
This free white paper will teach you about the most important server room monitoring features, and how to avoid the common pitfalls associated with installing a network monitoring system.