Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayA communication network protocol is a system of digital rules for message exchange within or between computers. In the telecom world, knowing what protocol your equipment "speaks" is a very important point, since it's the language that your RTU (Remote Telemetry Unit) and master station use to communicate with each other.

In other words, communication protocols allow monitored devices to exchange information with monitoring devices. However, each device must support the same protocol in the same version, and any differences might result in communication errors.
If you're starting to research about remote monitoring system, you probably noticed that manufacturers select which protocols their equipment will conform to. This means that you'd be choosing not only your monitoring solution but the protocol used to support it. There are two major types of protocols that devices use: open and proprietary.
Here, at DPS, we've provided customizable remote monitoring devices for more than 30 years, and we've seen all kinds of scenarios of clients using both types of protocols. Since our clients can choose which protocol they want in their monitoring system solutions, we know that both open and proprietary protocols have their benefits and drawbacks.
Also, we're not invested in one option over another. Both can be used with successful outcomes for clients. Because of that, we want to give you impartial insights about each type of protocol and help you evaluate your unique needs before making a choice.
Let's dive into some of the pros and cons of open protocols vs. proprietary protocols, so at the end of the day you can make an informed decision.
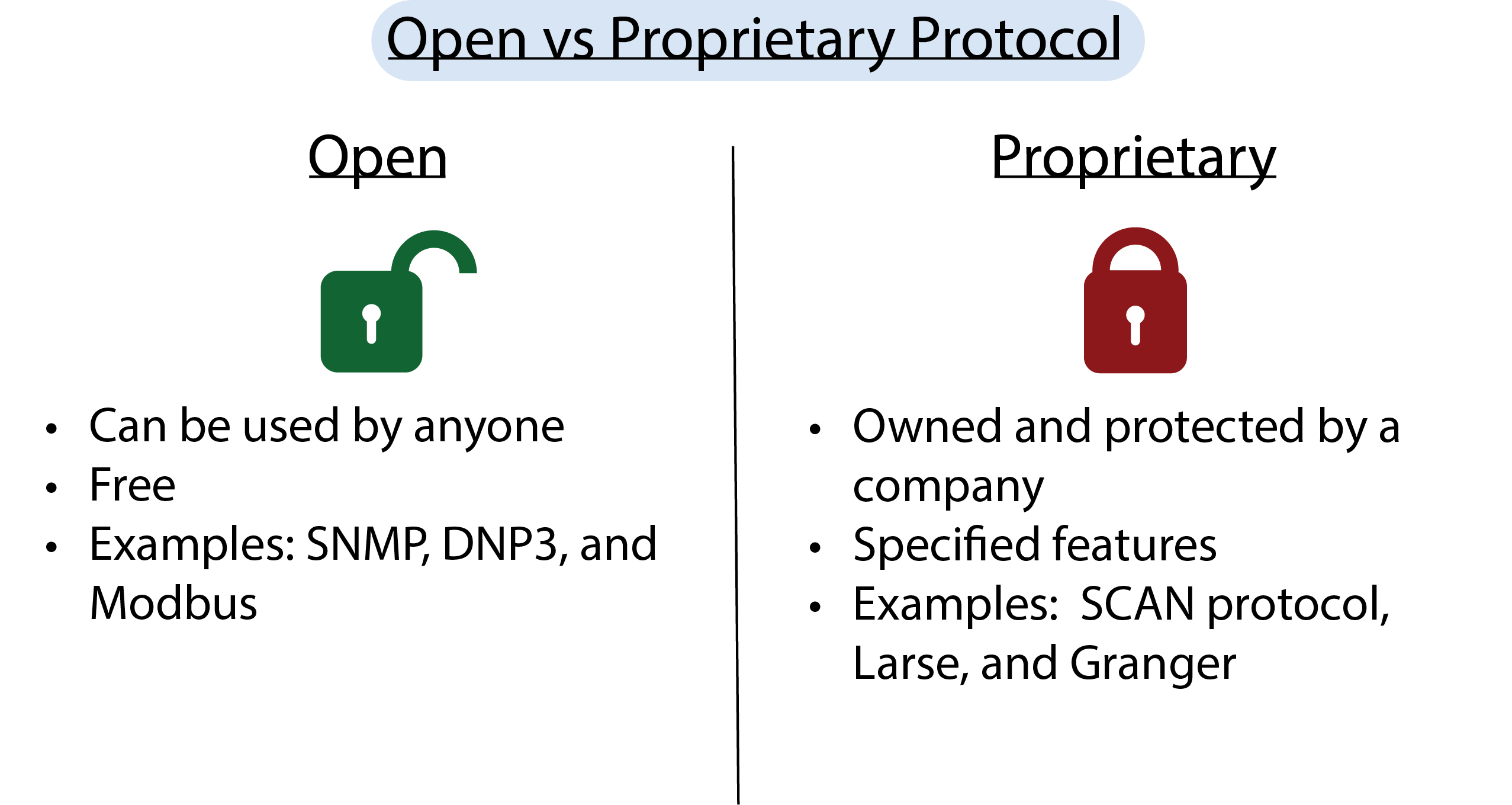
The open protocol definition is very simple. These are the kind of protocols that can be included in a wide range of device types from any equipment vendor. What this means is that manufacturers that choose to adopt an open protocol want to achieve protocol interoperability when they design their equipment's functionality and capabilities.
Examples of open protocols are: SNMP, DNP3, and Modbus.
Open protocols are transforming the landscape of technology by offering a myriad of benefits that enhance flexibility, accessibility, and innovation.
Can be used by anyone
Open protocols are rather universal - they can be used by anyone rather than one entity or company. An open protocol is the one that the manufacturer publishes this information for anyone to see and use. You can use this information freely without being charged and without any conditions.
These protocols are embedded in some of the world's most common technologies, such as WiFi and Bluetooth. Because the technology is public knowledge, most technicians can work on open protocols with ease, making them highly accessible for a range of applications.
You'll avoid vendor lock-in
Remote monitoring systems that use open protocols allow for the network manager to choose between a wider selection of manufacturers who supply devices that talk the same language to communicate with each other. Open protocol systems can be maintained by companies other than the system provider.
This flexibility extends to component sourcing as well. With components available from a wide variety of manufacturers, you're not tied to a single vendor. This ensures you can select the most optimal parts for your needs, enhancing both choice and cost-efficiency.
Higher flexibility
Since a very large number of different devices support open standard protocols, it's easier to make them work together. Open protocol systems offer a higher degree of networking flexibility, with more integration options between existing and new gear. This means that you can add new devices (independent of the vendor) to your existing network. You can choose between a variety of different vendors for the monitoring solution that best fits your needs - in terms of technical requirements and budget as well.
In the wake of the fourth wave of computing and IoT, open protocols are paving the way for truly effective systems, exemplified by innovations like Bluetooth mesh. Released in 2017, Bluetooth mesh provides an open standard foundation for groundbreaking IoT solutions, showcasing the innovative potential that open protocols bring to the table.
By harnessing these advantages, open protocols not only promote a more interconnected technological environment but also drive forward the next generation of technological innovation.
Since open protocols have their technical information disclosed for anyone, it's much easier for hackers to study these protocols to find out how to access and control your remote monitoring network.
Although most of them offer security features such as authentication and cryptography, it's never a total guarantee that a hacker won't be able to find a breach on a protocol that they can have easy access to.
Normally, devices can communicate with one another without a problem when they are from the same single manufacturer because they'll probably support the same proprietary network. This means that proprietary protocols are owned and protected by a determined company, and devices supporting this protocol can only communicate with other equipment supporting the same protocol.
Proprietary protocol examples are SCAN protocol, Larse, and Granger.
Proprietary protocols typically offer some specific features and capabilities. To compete with open protocols, they aim to appeal to people that need some level of personalization.
These protocols can include custom upgrades, functionalities, and tools.
Opting for a solution from a manufacturer of proprietary protocol systems will give you components that have been designed to work together.
This means that all elements of their devices are perfectly compatible with each other since they are designed to use the same language of communication. If you plan to deploy gear that uses only this same proprietary protocol, all of your systems should integrate smoothly.
When you work with a proprietary protocol, it basically means that your equipment is running on a unique protocol used only by your specific vendor. It makes it difficult to add devices from other vendors to your system later, and you'll likely be restricted to this one supplier for support and purchase of future products.
In other words, proprietary protocols lock customers in and take away their freedom of choice to expand their system with different vendors.
Here's how compatibility issues play a role:
Restrictive Installations: These protocols often restrict you to installing components exclusively from the original company. This limits your ability to choose from a variety of products that might better suit your needs.
Repair Limitations: Any necessary repairs will typically require associates from the same company, leading to potential delays and increased dependence on a single provider.
Cost and Performance Concerns: Such restrictions can result in higher costs over time. You're cornered into using potentially suboptimal components, which might not offer the best performance or value.
By understanding these limitations, you can better assess whether a proprietary protocol aligns with your long-term goals and flexibility needs.
Proprietary protocols are usually perceived as traps. That's because most proprietary systems require recurring license fees, so the costs add up.
Recurring fees involve paying some amount of money over some length of time. There are different kinds of recurring fees. Some of them will require you to pay a moderate initial purchase price and then you pay a smaller fee month by month, for as long as you're using the system.
There are actually numerous kinds of recurring fee variations. There are even more modern models where you don't pay anything upfront, but you're required to sign control to pay some kind of monthly fee forever - as long as you want to use the proprietary protocol.
This all means that you're tied for the duration of the contract and even after these years if you decide to change to another system later.
Plus, you'll be dependent on only this company for maintenance, support, updates, and upgrades. And you may endure poor service, slow response times, and ongoing maintenance costs - after all, you depend on them to have your system up and running.
You need to make sure you fully understand what you're committing to, and know that your proprietary protocol vendor is not going to trap you in the future. Licensing fees can have a huge impact on your budget, and it's important to calculate the true cost of ownership for your remote monitoring system.
The bottom line here is that if you need the freedom to choose between vendors, and to integrate all your different devices, choosing to work with an open protocol might be the best choice for you.
It may sound like an open protocol would always be the preferable option. However, it doesn't necessarily mean that proprietary protocols are bad, or that they can't be your right choice. If you need the guarantee of optimum performance between your devices, a proprietary protocol might offer that for you.
The bottom line here is that it doesn't matter what kind of devices you need to monitor in your remote site or facility, some pros and cons need to be weighed in when you're choosing which kind of protocol you want to work with.
As an experienced remote monitoring solutions provider, we've seen all kinds of different scenarios, and we know that oftentimes our clients don't even really have the choice to choose between working only with an open or closed protocol. Most of them inherited a network full of mixed legacy devices, running on many different protocols.
A full swap-out of older devices is normally out of reach for many companies, simply because is too expensive to replace all the legacy monitoring equipment with modern devices at once.
Even if you think you're stuck with your older system running on different protocols, we can show you a way out to make all of them coexist.
In our Intelligent SNMP Legacy Integration white paper, we will present you with proven, field-tested protocol mediation solutions that will integrate your equipment running on different protocols. Download your free copy today and learn more about how you can avoid spending a fortune on replacement devices, and without sacrificing essential alarm capabilities.

Morgana Siggins
Morgana Siggins is a marketing writer, content creator, and documentation specialist at DPS Telecom. She has created over 200 blog articles and videos sharing her years of experience in the remote monitoring industry.